Cyber Incident Reporting For Critical Infrastructure Act Of 2021 – On March 15, 2022, U.S. President Biden signed the Critical Infrastructure Cyber Incident Reporting Act of 2022 as part of a larger spending bill. The law is the most sweeping cybersecurity regulation for the U.S. private sector to date, requiring critical industry sectors to report incidents to the Cybersecurity and Infrastructure Security Agency (CISA).
The United States passed the bill in the shadow of the conflict in Ukraine, and many in the country are concerned about an increase in cyberattacks by spies and criminals. Importantly, the law, which was 10 years in the making, aims to uncover how many companies are falling victim to cyberattacks, something that is difficult to quantify in the United States. Thing.
Cyber Incident Reporting For Critical Infrastructure Act Of 2021

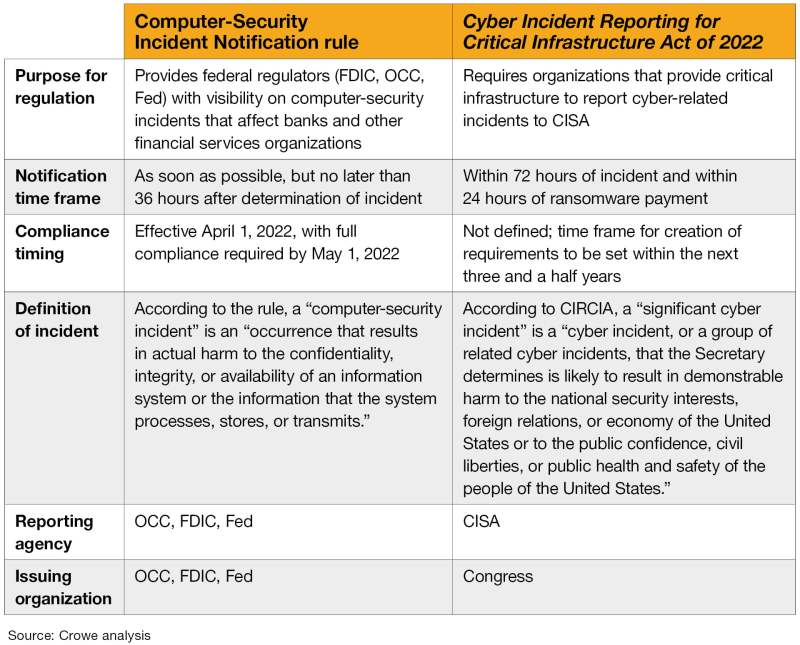
Although the law’s incident reporting requirements will not go into effect until CISA implements specific rules (which could take up to 42 months), it is important to understand what the new law is. Additionally, covered organizations should pay close attention to his CISA ruling as there are some ambiguities in the law, which CISA will clarify in the future.
Cyber Incident Reporting Act: What It Means For Your Organization
CISA is a U.S. federal agency under the Department of Homeland Security that was created in 2018 with the mission of strengthening the security, resiliency, and reliability of the nation’s cybersecurity and communications infrastructure.
The agency plays an important role in implementing the new Cyber Incident Reporting Act. This is because there are several areas of ambiguity regarding covered entities that must comply with the law, which cyber incidents must be reported under the law, and the timeline for reporting for which CISA is responsible. To define. These definitions ultimately determine who and what the law covers, what is required in that case, and how the law is enforced.
Additionally, this law will not become effective until CISA issues a final rule. The agency has 24 months to issue a notice of proposed rulemaking and 18 months from that notice to issue a final rule.
This law applies to the critical infrastructure sector as defined in Presidential Policy Directive 21 and includes:
Cyber Incident Reporting — Fbi
Notably, the law does not specify that all these sectors are subject to compliance. It is now CISA’s responsibility to define specifically which of these sectors must comply with the new law based on the impact of cyberattacks on national security, economic security, and public health and safety. is. CISA will also need to consider the extent to which the disruption will impact critical operations within the United States. Organizations in sectors that CISA has deemed covered by this law are known as “covered entities.”
Importantly, this law only partially defines what is meant by a major cyber incident. It defines a cyber incident as an unauthorized event that endangers the integrity, confidentiality, or availability of an information system or the information system itself, actual or imminent.
As part of its implementing regulations, CISA is now required to define what constitutes a “major” cyber incident reportable under the Act. Minimum thresholds for major cyber incidents include:

Finally, if a covered entity makes a ransom payment (which may include money or other property or assets) in connection with a ransomware attack, it may be required to comply with the Critical Infrastructure Cyber Incident Reporting Act of 2022. A report is also required. Even if the resulting payment does not meet the definition of a major cyber incident, organizations must still report the payment to CISA.
Improving The Cybersecurity Of Critical Infrastructure
A covered company must report it to CISA within 72 hours from when it “reasonably believes” a major cyber incident has occurred. The law does not define “reasonably believe,” nor does it require CISA to define it. Therefore, this may be determined in the process of actually applying the law.
However, CISA will need to define the details of what the report must contain and whether there are any restrictions on the format or delivery of the report. The law requires organizations to include at least the following when reporting serious cyber incidents to CISA:
Similar requirements apply in the case of ransom payments. Eligible companies must issue a report to his CISA within 24 hours after payment. Pending additional definitions from CISA, reports must include at least all of the above information, plus the following:
If material new or different information arises after the initial report, the organization will alert CISA (even if it means issuing multiple reports) until the incident is closed and fully mitigated and resolved. must continue. Organizations should also maintain all data related to cyber incidents and ransom payments based on guidance that CISA is still defining.
Cyber Breach Reporting To Be Required By Law For Better Cyber Defense: Pwc
One of the unique elements of the Critical Infrastructure Cyber Incident Reporting Act of 2022 is that it also provides protections for organizations issuing reports. These protections are designed to protect your organization from certain risks, such as public access and litigation. They include:
Excluded entities that wish to voluntarily file a report with CISA after a cyber incident or ransom payment may receive similar protections by doing so.
What types of incidents can trigger a report under the Critical Infrastructure Cyber Incident Reporting Act of 2022?

Covered entities that experience significant cyber incidents or make ransomware payments are required to issue a report to CISA. The definition of a major cyber incident has not yet been defined, but it may include the following types of events:
Virginia Lawyer April 2023 Page 18
During a DDoS attack, hackers create an influx of fake traffic to a server, network, or infrastructure, flooding it with visitors and halting normal operations. DDoS attacks themselves do not compromise security of any kind, but they can disrupt operations for long periods of time and are often used as a thwart for other types of attacks that compromise security protections.
Zero-day attacks occur when hackers exploit existing vulnerabilities in software. This vulnerability may be unknown to the developer or organization that owns the software, or it may be known and not yet patched. Zero-day attacks are very difficult to detect, and as long as the attack continues, hackers can potentially impact networks, data, or programs associated with the flawed software.
In a ransomware attack, hackers use malware to steal data and imprison it in exchange for a ransom payment. If the victim pays the ransom, the data may or may not be returned. Regardless of the outcome, the targeted company must report the ransom payment to his CISA.
CISA is the first line of defense in enforcing the Critical Infrastructure Cyber Incident Reporting Act of 2022, but CISA cannot impose financial penalties. Rather, government agencies have the power to request information and issue subpoenas in response to organizations suspected of not complying with the law.
Cybersecurity And Infrastructure Security Agency
If an organization does not comply with these orders, CISA may refer the matter to the U.S. Attorney General. At that point, the U.S. attorney general can enforce the subpoena through civil litigation, hold the organization in contempt of court, or refer the matter to criminal prosecution.
While much depends on the covered entity and CISA’s definition of a major cyber incident, there are some immediate steps that organizations potentially subject to this law can take to ensure compliance.
For example, major cyber incidents and ransomware payments have 72-hour and 24-hour reporting timelines, respectively, and require quick responses. This means organizations must be ready to act quickly. Part of this action includes being able to determine whether an incident meets defined thresholds for issuing a report. Additionally, organizations must issue supplemental reports as new information becomes available, so teams must be prepared for ongoing efforts. Given all this, organizations need to be proactive in preparing response plans, assigning clear responsibilities to team members for each part of those plans, and streamlining workflows to coordinate and record. there is.

Specifically, organizations that may be defined as covered entities under this law must begin preparing for three key stages of incident response:
Elections Systems Are Critical Infrastructure And Must Be Protected
Preparation focuses on proactively preparing an incident response plan so that your team can quickly take action when an incident occurs. Doing so will reduce associated costs and facilitate a return to normal business.
Key preparedness activities include reviewing the requirements outlined in relevant regulations and customer and partner agreements, as well as establishing a clear incident response plan to meet those requirements should an incident inevitably occur. Includes providing an overview.
Response centers around the actions an organization takes when an incident occurs. With the new law in the United States, a quick response is critical to diagnosing the incident as meeting the reporting criteria and allowing him to issue a report to CISA within the specified period. Additionally, faster responses help reduce the loss of trust from customers and the market.
Key response activities include determining what happened, including whether regulatory reporting standards were met, when and how it occurred, and the potential consequences. and assigning and carrying out tasks to comply with regulatory or contractual obligations, including issuing reports in accordance with applicable law and taking steps to resolve issues where possible. Also included.
What Is Circa?
Continuing management recognizes that
Cyber critical infrastructure, cyber incident reporting act of 2021, cyber attack critical infrastructure, critical incident reporting system, fbi cyber incident reporting, cyber threats to critical infrastructure, critical infrastructure cyber security, critical infrastructure protection act, dod cyber incident reporting, cyber attacks on critical infrastructure, cyber incident reporting act, cyber incident reporting